如果一个大公司他们公司在中国有几十家子公司,而这些子公司的局域网需要和总公司的内网通信,现在让你帮他们设计子公司与总公司的××× 网络,并且希望总公司和分公司之间能够使用动态路由。由此,引出了Dynamic Multipoint ××× (DM×××). 完成DM××× 的功能,需要以下两个技术来实现: 1.multipoint GRE (mGRE) 2.Next Hop Resolution Protocol (NHRP) 在mGRE中,核心路由器称为Hub,而分支路由器称为spoke,在配置时,Hub上必须将GRE 接口类型指定为multipoint GRE (mGRE),在Hub上配置mGRE接口,则不需要为每个peer单独建立一条GRE接口。 无论mGRE 中Hub 要和多少个spoke 连接,所有Hub 和所有spoke 的IP 地址必须在同网段 。在mGRE 中,Hub 的物理IP 必须固定, Spoke 的物理IP 可随意。 Next Hop Resolution Protocol (NHRP)
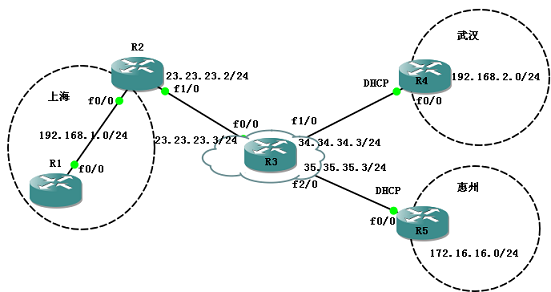
对于mGRE,它利用了一个单独的协议去解决Hub 获得spoke 真实IP 地址的问题,这个协议就是Next Hop Resolution Protocol (NHRP),因为只要动态IP 地址方先向静态IP 地址方发送数据,静态IP 地址方就能够知道动态IP 地址方的地址是什么,所以mGRE 的Hub 就可以在spoke 发给自己的数据包中得知spoke 的真实IP 地址,根据这个原因,NHRP 就强制规定spoke必须主动向Hub 告知自己的真实IP 地址,这样就能使HUB 轻松获得所有spoke的真实IP 地址,从而正常建立mGRE 中的所有GRE,最终实现DM×××。 如下图实验:我们以三地测试DMVPM,上海是Hub,武汉和惠州是spoke
en conf t line con 0 no exec-t exit host r1 int f0/0 no sh ip add 192.168.1.1 255.255.255.0 exit ip route 0.0.0.0 0.0.0.0 192.168.1.2
===============================R2================================== R2>en R2#conf t Enter configuration commands, one per line. End with CNTL/Z. R2(config)#line con 0 R2(config-line)#no exec-t R2(config-line)#exit R2(config)#host r2 r2(config)#int f0/0 r2(config-if)#no sh r2(config-if)#ip add 192.168.1.2 255.255.255.0 r2(config-if)#int f1/0 r2(config-if)#no sh r2(config-if)#ip add 23.23.23.2 255.255.255.0 r2(config-if)#exit r2(config)#ip route 0.0.0.0 0.0.0.0 23.23.23.3 r2(config)# r2(config)#end
r2(config)# r2(config)#crypto r2(config)#crypto isa r2(config)#crypto isakmp pol r2(config)#crypto isakmp policy 10 r2(config-isakmp)#encryption 3de r2(config-isakmp)#encryption 3des r2(config-isakmp)#hash sha r2(config-isakmp)#au r2(config-isakmp)#authentication pre r2(config-isakmp)#authentication pre-share r2(config-isakmp)#grou r2(config-isakmp)#group 2 r2(config-isakmp)#exit r2(config)#crypto isakmp key 6 dm*** address 0.0.0.0 r2(config)#crypto ipsec transform-set myset esp-3 r2(config)#crypto ipsec transform-set myset esp-3des esp-sha r2(config)#crypto ipsec transform-set myset esp-3des esp-sha-hmac r2(cfg-crypto-trans)#exit r2(config)#crypto ipsec profile cisco r2(ipsec-profile)#set transform-set myset r2(ipsec-profile)#exit r2(config)#int tunne r2(config)#int tunnel 2 r2(config-if)#no sh r2(config-if)#band r2(config-if)#bandwidth 1000 r2(config-if)#ip add 10.1.1.1.2 255.255.255.0 r2(config-if)#ip mtu 1400 r2(config-if)#ip nh r2(config-if)#ip nhrp authentication *** --设置认证密码,同一个mGRE 中所有点(包括所有
Hub和所有spoke)的密码必须一致 r2(config-if)#ip nhrp map multicast dynamic -- 自动将spoke 的地址加入组播映射中,否则
与spoke 之间使用组播的路由协议不能正常运行 r2(config-if)#ip nhrp network-id 2--配置网络标识号,等于是启用NHRP,同一个mGRE 中所有点 (包括所有Hub 和 所有spoke)的号码必须一致 r2(config-if)#no ip split-horizon eigrp 100 r2(config-if)#tunnel sour r2(config-if)#tunnel source 23.23.23.2 r2(config-if)#tunnel mode gre multipoint --定义mGRE接口 r2(config-if)#tunnel key 10000--定义Tunnel接口ID,此步并不是必须的,若定义了,Hub和
spoke必须一致 r2(config-if)#tunnel protection ipsec pro r2(config-if)#tunnel protection ipsec profile cisco r2(config)#exit r2(config)#
r2(config)#router eigrp 100 r2(config-router)#no au r2(config-router)#net 192.168.1.0 0.2 0.0.0.0 r2(config-router)#net 10.1.1.2 0.0.0.0 r2(config-router)#exit
r2(config)#int tunnel2 r2(config-if)#no ip next-hop-self eigrp 100--让R4到R5的下一跳不经过Hub端,直接发往spoke端R5 r2(config-if)#
===================================Internet================================= en conf t line con 0 no exec-t exit host Internet int f0/0 no sh ip add 23.23.23.3 255.255.255.0 int f1/0 no sh ip add 34.34.34.3 255.255.255.0 int f2/0 no sh ip add 35.35.35.3 255.255.255.0 exit service dhcp ip dhcp pool ***1 network 34.34.34.0 255.255.255.0 default-r 34.34.34.3 exit ip dhcp pool ***2 network 35.35.35.0 255.255.255.0 default-r 35.35.35.3 exit ip dhcp excluded-address 34.34.34.3 ip dhcp excluded-address 35.35.35.3 ================================R4==================================== en conf t line con 0 no exec-t exit host r4 int f0/0 no sh ip add dhcp exit ip route 0.0.0.0 0.0.0.0 34.34.34.3 r4(config)#int lo 0 r4(config-if)#no sh r4(config-if)# *Mar 1 00:04:23.831: %LINEPROTO-5-UPDOWN: Line protocol on Interface Loopback0,
changed state to up r4(config-if)#ip add 192.168.2.4 255.255.255.0 r4(config-if)# r4(config-if)# r4(config-if)# r4(config-if)#end r4# Enter configuration commands, one per line. End with CNTL/Z. r4(config)#crypto isakmp policy 10 r4(config-isakmp)#encryption 3des r4(config-isakmp)#hash sha r4(config-isakmp)#aut r4(config-isakmp)#authentication pre r4(config-isakmp)#authentication pre-share r4(config-isakmp)#group 2 r4(config-isakmp)#exit r4(config)#crypto isakmp key 6 dm*** address 0.0.0.0 r4(config)#crypto ipse transform-set myset esp-3des esp-sha-hmac r4(cfg-crypto-trans)#exit r4(config)#crypto ipsec profile cico r4(ipsec-profile)#set tran myset r4(ipsec-profile)#exit r4(config)#int tunnel 4 r4(config-if)#bandwidth 1000 r4(config-if)#ip add 10.10.1.4 255.255.255.0 r4(config-if)#ip mtu 1400 r4(config-if)#ip nhrp authentication *** r4(config-if)#ip nhrp map 10.1.1.2 23.23.23.2 -Hub 的GRE 接口地址100.1.1.1 和公网IP 地
址12.1.1.1 静态映射绑定 r4(config-if)#ip nhrp map multicast 23.23.23.2-开启能向Hub 发送组播的功能,从而开启动态
路由协议的功能 r4(config-if)#ip nhrp net r4(config-if)#ip nhrp network-id 2 r4(config-if)#ip nhrp nhs 10.1.1.2--将Hub 路由器指定为NHRP Server r4(config-if)#tunnel source f0/0 r4(config-if)#tunnel mode gre multipoint r4(config-if)#tunnel key 10000 r4(config-if)#tunnel protection ipsec profile ciaco r4(config-if)#exit r4(config)#router eigrp 100 r4(config-router)#no au r4(config-router)#net 10.1.1.4 0.0.0.0 r4(config-router)#net 192.168.2.4 0.0.0.0 r4(config-router)#end
=================================R5=================================== en conf t line con 0 no exec-t exit host r5 int f0/0 no sh ip add dhcp int lo 0 no sh ip add 172.16.16.5 255.255.255.0 exit ip route 0.0.0.0 0.0.0.0 35.35.35.3 r5(config)#crypto isakmp policy 10 r5(config-isakmp)#en 3des r5(config-isakmp)#hash sha r5(config-isakmp)#authentication pr r5(config-isakmp)#authentication pre-share r5(config-isakmp)#group 2 r5(config-isakmp)#exit r5(config)#crypto isakmp key 6 dm***add add 0.0.0.0 r5(config)#crypto ipsec transform-set myset esp-3des esp-sha-hmac r5(cfg-crypto-trans)#exit r5(config)#crypto ipsec profile cisco r5(ipsec-profile)#set transform-set myset r5(ipsec-profile)#exit r5(config)#int tunnel 5 r5(config-if)#no sh r5(config-if)#bandwidth 10000 r5(config-if)#ip add 10.1.1.5 255.255.255.0 r5(config-if)#ip mtu 1400 r5(config-if)#ip nhrp au r5(config-if)#ip nhrp authentication *** r5(config-if)#ip nhrp map 10.1.1.2 23.23.23.2 r5(config-if)#ip nhrp map mu r5(config-if)#ip nhrp map multicast 23.23.23.2 r5(config-if)#ip nhrp network-id 2 r5(config-if)#ip nhrp nhs 10.1.1.2 r5(config-if)#tunnel soure f0/0 r5(config-if)#tunnel mode gre multipoint r5(config-if)#tunnel key 1 r5(config-if)#tunnel key 10000 r5(config-if)#tunnel protection ipsec profile cisco r5(config-if)#exit r5(config)#int tunnel 5 r5(config-if)#band r5(config-if)#bandwidth 1000 r5(config-if)#end r5(config)#route eigrp 100 r5(config-router)#no au r5(config-router)#net 10.1.1.5 0.0.0.0
r5(config-router)#net 172.16.16.5 0.0.0.0 r5(config-router)#exit
r5(config)#end
实验调试:
r2调试
r2#sh crypto isakmp peers Peer: 34.34.34.1 Port: 500 Local: 23.23.23.2 Phase1 id: 34.34.34.1 Peer: 35.35.35.1 Port: 500 Local: 23.23.23.2 Phase1 id: 35.35.35.1
r2#sh crypto isakmp sa dst src state conn-id slot status 23.23.23.2 34.34.34.1 QM_IDLE 1 0 ACTIVE 23.23.23.2 35.35.35.1 QM_IDLE 2 0 ACTIVE
IKE SA成功建立
查看Hub 端R2 的NHRP 映射情况
r2#sh ip nhrp 10.1.1.4/32 via 10.1.1.4, Tunnel2 created 03:04:23, expire 01:35:12 Type: dynamic, Flags: authoritative unique registered NBMA address: 34.34.34.1 10.1.1.5/32 via 10.1.1.5, Tunnel2 created 02:46:34, expire 01:52:59 Type: dynamic, Flags: authoritative unique registered NBMA address: 35.35.35.1
r2#sh ip nhrp brief Target Via NBMA Mode Intfc Claimed 10.1.1.4/32 10.1.1.4 34.34.34.1 dynamic Tu2 < > 10.1.1.5/32 10.1.1.5 35.35.35.1 dynamic Tu2 < >
Hub端已经成功存在R4和R5的mGRE接口10.1.1.4,10.1.1.5对应的34.34.34.1,35.35.35.1的公网地址映射
spoke调试,以R4为例
r4#sh ip nhrp 10.1.1.2/32 via 10.1.1.2, Tunnel4 created 03:12:17, never expire Type: static, Flags: authoritative used NBMA address: 23.23.23.2
r4#sh ip nhrp brief Target Via NBMA Mode Intfc Claimed 10.1.1.2/32 10.1.1.2 23.23.23.2 static Tu4 < >
spoke端成功建立Hub端mGRE接口10.1.1.2到23.23.23.2公网的映射,并且是静态映射
EIGRP调试
Hub端
r2#sh ip eigrp neighbors IP-EIGRP neighbors for process 100 H Address Interface Hold Uptime SRTT RTO Q Seq (sec) (ms) Cnt Num 1 10.1.1.4 Tu2 11 02:49:49 254 1524 0 9 0 10.1.1.5 Tu2 12 02:49:50 251 1506 0 8
成功建立邻居关系
r2#sh ip route Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2 i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2 ia - IS-IS inter area, * - candidate default, U - per-user static route o - ODR, P - periodic downloaded static route
Gateway of last resort is 23.23.23.3 to network 0.0.0.0
23.0.0.0/24 is subnetted, 1 subnets C 23.23.23.0 is directly connected, FastEthernet1/0 172.16.0.0/24 is subnetted, 1 subnets D 172.16.16.0 [90/15488000] via 10.1.1.5, 02:50:41, Tunnel2 10.0.0.0/24 is subnetted, 1 subnets C 10.1.1.0 is directly connected, Tunnel2 C 192.168.1.0/24 is directly connected, FastEthernet0/0 D 192.168.2.0/24 [90/15488000] via 10.1.1.4, 02:50:41, Tunnel2 S* 0.0.0.0/0 [1/0] via 23.23.23.3
学到武汉和惠州的内网路由
连通测试以r1为例
r1#ping *Mar 1 04:02:08.310: %SYS-5-CONFIG_I: Configured from console by console r1#ping 192.168.2.4
Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.2.4, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 84/127/160 ms r1#ping 172.16.16.5
Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 172.16.16.5, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 92/140/204 ms r1#
r1#tra 172.16.16.5
Type escape sequence to abort. Tracing the route to 172.16.16.5
1 192.168.1.2 44 msec 48 msec 12 msec 2 10.1.1.5 176 msec * 204 msec 成功通过隧道和惠州通信
r1#tra 192.168.2.4
Type escape sequence to abort. Tracing the route to 192.168.2.4
1 192.168.1.2 84 msec 52 msec 20 msec 2 10.1.1.4 112 msec * 140 msec
成功通过隧道和武汉通信